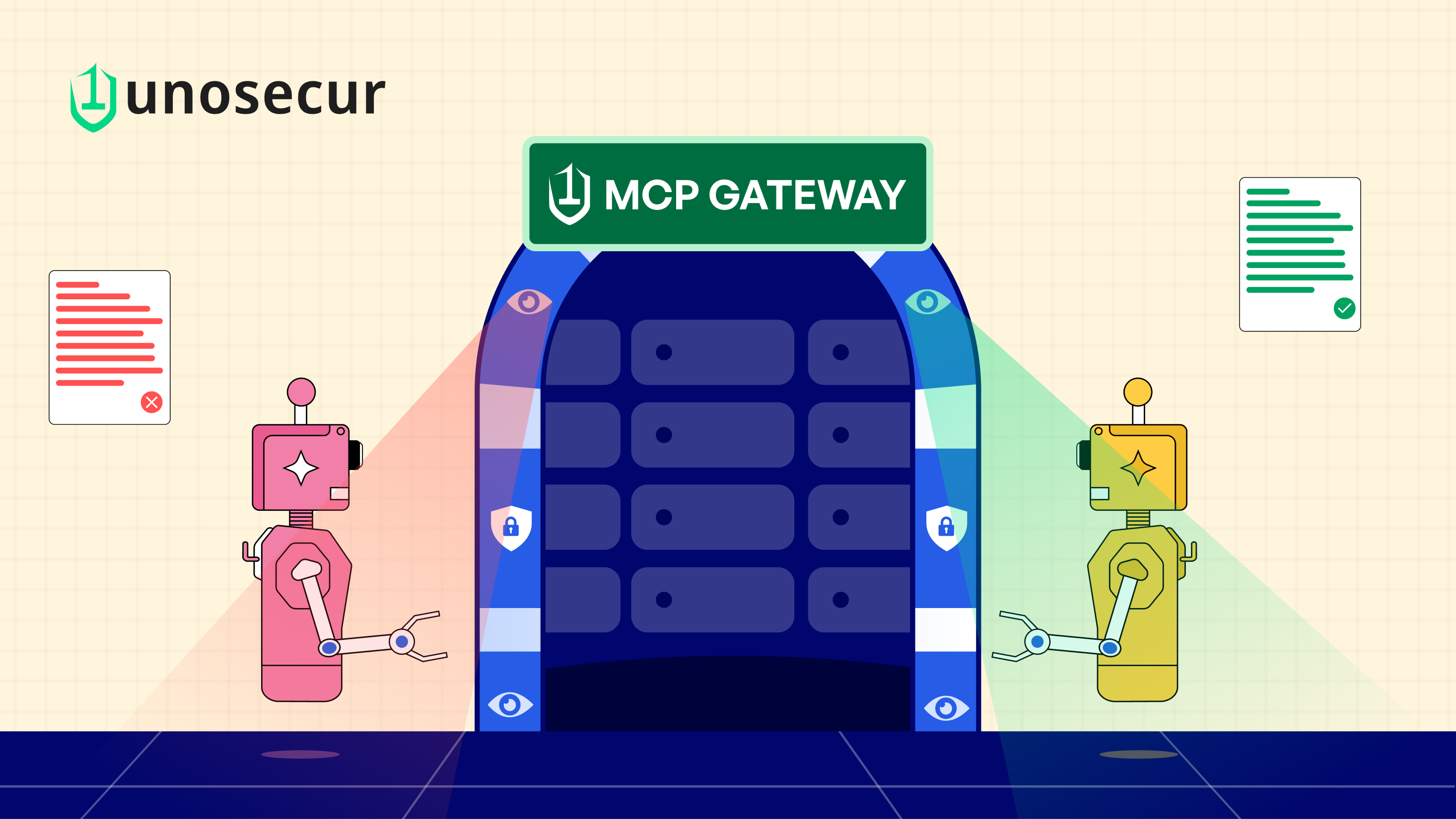
See every identity
Stop every threat
Real-time, continuous identity security for modern enterprises

































Secure your identity attack surface with AI-powered visibility
Unosecur identifies the blast radius for both human and non-human identities in real time. Preventing account takeovers and privilege abuse in under 10 mins.

Unified Identity Fabric:
Total visibility of your identity stack
Total cloud and on-premise identity visibility and management in a single platform. Instantly stop identity-based breaches in complex, regulated environments with prioritized, context-rich insights aligned to MITRE ATT&CK.
Technology and service integrations










































































Simplified hybrid identity management
Unosecur closes security gaps across cloud, on-premises, and containerized environments. Our AI engine detects abnormal identity behavior as it unfolds, stopping attacks
before they escalate.
Agentless and real-time
Deploy Unosecur without agents and connect your environments within minutes.
Breach prevention
Protect against identity-based threats for both human and non-human accounts. Automate fixes to neutralize access risks before they become breaches.
No-code workflows
for IAMOps
Speed up detection, remediation, and incident response using pre-built, coding-free workflows that align security and business teams.
Use Cases
Discover how Unosecur boosts identity security and helps meet compliance needs.
Identity Threat Detection and Response
Leverage MITRE ATT&CK model-based, real-time threat detection and response (ITDR) to swiftly identify malicious actors and stop attack chains in their tracks.
Identity Security Posture Management
Continuously monitor access controls, permissions, and identity activities. Fix security gaps using simplified yet granular no-code workflows to strengthen your identity security posture.
Identity Least Privileges Implementation
Dynamically adjust permissions in real time to enforce least privilege at scale (powered by GenAI) across multiple cloud providers. Stop entitlement creep and reduce your attack surface.
Identity Privilege Access Management
Manage privileged access effectively, granting or revoking permissions based on role requirements and security policies. Leverage Slack integration and email communication, ensuring maximum business continuity.
Identity Audit and Compliance
Maintain continuous compliance with regulatory standards using Unosecur’s comprehensive visibility into identity activity and access controls. Identify and remediate compliance gaps directly from the platform.
What our customers say
FAQs
Unosecur is designed to benefit a wide range of professionals involved in cloud security and identity management, including CISOs, DevOps, DevSecOps, IT managers, and SOC teams. Furthermore, Unosecur has developed AI-assisted low-code/no-code workflows, rendering them accessible to non-technical team members. This means that anyone in your organization can easily manage and enhance security measures without needing extensive coding knowledge.
Integrating Unosecur with your existing cloud infrastructure is straightforward and non-intrusive. Unosecur is agentless, meaning it requires no software agents to be installed on your systems. Instead, it seeks read-only permissions to access your cloud environment. This allows Unosecur to pull data in near real-time, ensuring up-to-date identity management and security without disrupting your current operations. The integration process is designed to be seamless, minimizing any potential impact on your workflows.
Yes, Unosecur supports AWS, Azure, and GCP, ensuring consistent security and identity management across all major cloud providers. One of Unosecur’s key features is its single pane of glass view, which allows you to manage and monitor security policies and identities across multiple cloud environments from a unified interface. This holistic view simplifies administration, enhances visibility, and ensures that your security posture remains robust and cohesive, regardless of the cloud platform in use.
Unosecur's real-time identity-based threat detection stands out due to its advanced capabilities developed in our state-of-the-art in-house SOC lab. This facility has enabled us to build robust and highly sophisticated threat detection mechanisms that monitor and analyze identity-related activities continuously. Unlike many competitors that may rely on periodic scans or have slower threat detection systems, Unosecur provides near-instantaneous responses to potential threats, significantly enhancing security and minimizing risks. Our dedicated SOC lab ensures that we stay ahead of emerging threats and continuously improve our detection capabilities, offering a superior level of protection compared to other products on the market.
Unosecur meets major compliance standards SOC 2 and ISO 27001, confirming that our security, risk management, and data protection controls are robust and globally recognized. Compliance with GDPR and HIPAA standards ensures that we rigorously protect sensitive personal and healthcare data. Additionally, our trusted cloud provider badge from the Cloud Security Alliance validates our best practices in cloud security, underscoring our commitment to maintaining a secure environment for our clients.
Yes, Unosecur is available as a SaaS solution, allowing you to benefit from quick setup, scalability, and seamless updates without managing hardware or infrastructure.
With Unosecur, data can be stored in your own environment (on-premises or in the cloud) or in our secure cloud infrastructure. All data is encrypted in transit and at rest, ensuring security at every level.
Setting up integrations is simple through the Unosecur dashboard. Just navigate to the "Integrations" tab, select the tool you want to integrate, and follow the guided setup instructions. You can also refer to our detailed documentation for API-based integrations.
Check out our blog
Your source for the latest insights and updates on advanced security solutions

















.png)